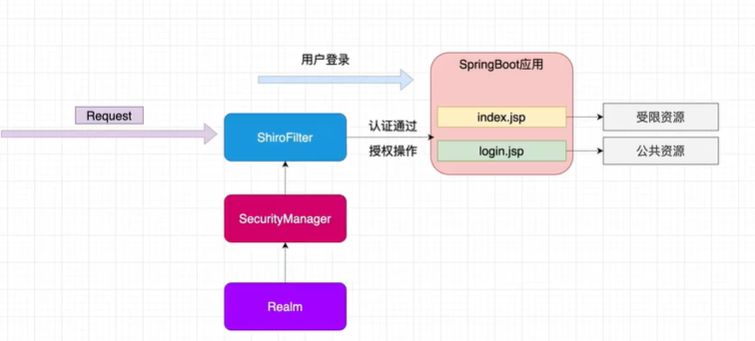
1 整体思路
2 配置环境
1.1 创建SpringBoot项目
2.2 引入shiro依赖
1 | <!-- 引入shiro依赖--> |
2.3 修改视图
application.properties文件
1 | # 应用名称 |
2.4 修改配置
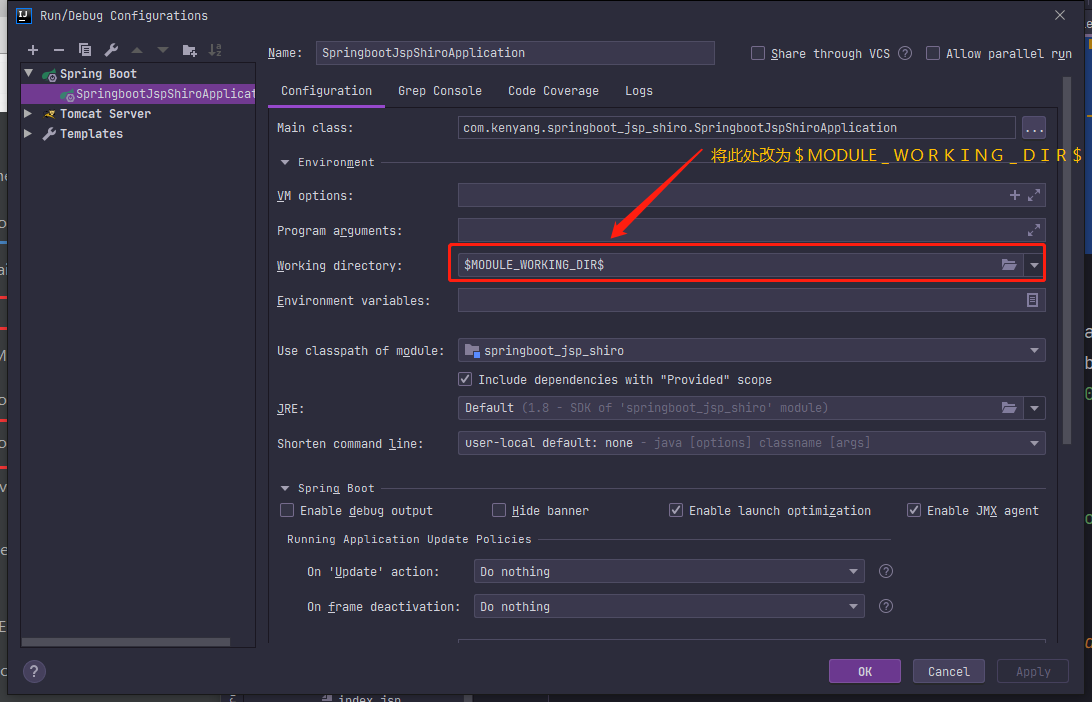
JSP与IDEA与SpringBoot存在一定的不兼容,修改此配置即可解决。
3 简单使用
3.1 创建配置类
1 | /** |
3.2 配置自定义Realm
1 | //自定义realm |
3.3 JSP文件
index.jsp
1 | <% contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %> |
login.jsp
1 | <% contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %> |
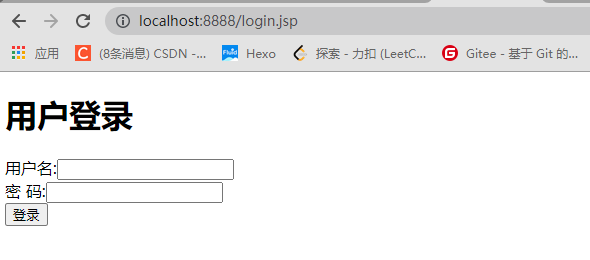
3.4 简单测试
- 注意:
- 默认在配置好shiro环境后默认环境中没有对项目中任何资源进行权限控制,所以现在项目中所有资源都可以通过路径访问
- 加入权限控制后,访问index,则会自动跳转到login.jsp中
- “/**”代表拦截项目中一切资源 “authc”代表shiro中的一个filter的别名
4 常见过滤器
注意:shiro提供多个默认的过滤器,我们可以用这些过滤器来配置控制指定url的权限:
| 配置缩写 | 对应的过滤器 | 功能 |
|---|---|---|
| anon | AnonymousFilter | 指定url可以匿名访问 |
| authc | FormAuthenticationFilter | 指定url需要form表单登录,默认会从请求中获取username、password、rememberMe等参数并尝试登录,如果登录不了就会跳转到loginUrl配置的路径。我们也可以用这个过滤器做默认的登录逻辑,但是一般都是我们自己在控制器写登录逻辑的,自己写的话出错返回的信息都可以定制嘛 |
| authcBasic | BasicHttpAuthenticationFilter | 指定url需要basic登录 |
| logout | LogoutFilter | 登出过滤器,配置指定的url就可以实现退出功能,非常方便 |
| noSessionCreation | NoSessionCreationFilter | 禁止创建会话 |
| perms | PermissionAuthorizationFilter | 需要指定权限才能访问 |
| port | PortFilter | 需要指定端口才能访问 |
| rest | HttpMethodPermissionFilter | 将http请求方法转化成相应的动词来构造一个权限字符串 |
| roles | RolesAuthorizationFilter | 需要指定角色才能访问 |
| ssl | SslFilter | 需要https请求才能访问 |
| user | UserFilter | 需要已登录或“记住我”的用户才能访问 |
5 认证和退出的实现
5.1 login.jsp
1 | <% contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %> |
5.2 UserController
1 |
|
- 在认证过程中使用subject.login进行认证
5.3 自定义Realm
1 | //自定义realm |
5.4 ShiroConfig
主要的Shiro配置类中声明:哪些是需要验证的资源,哪些是公开的资源。
注意:先配置公共资源,后配置需要认证/授权的资源
此时认证功能没有md5和随机盐的认证
1 | /** |
6 MD5、Salt的认证实现
6.1 用户注册和随机盐处理
6.1.1 导入依赖
1 | <!--mybatis相关依赖--> |
6.1.2 application.properties
1 | = com.mysql.cj.jdbc.MysqlDataSource |
6.1.3 创建数据库
1 | SET NAMES utf8mb4; |
6.1.4 创建entity
1 |
|
6.1.5 创建DAO接口
1 |
|
6.1.6 开发mapper配置文件
注意:mapper文件的位置要在application.properties配置的目录下面
注意:mapper文件的命名与Dao接口保持一致
1 |
|
6.1.7 开发service接口
1 | public interface UserService { |
6.1.8 创建salt工具类
1 | public class SaltUtil { |
6.1.9 开发service实现类
1 |
|
6.1.10 开发Controller
1 |
|
6.1.11 设置公共资源
在ShiroConfig中添加
1 | map.put("/user/register","anon");//anon 设置为公共资源 |
6.1.12 测试
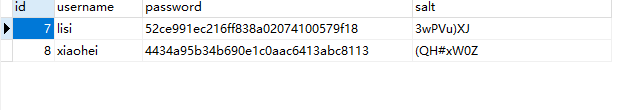
添加成功
6.2 开发数据库认证
6.2.1 开发DAO
1 |
|
6.2.2 开发mapper配置文件
1 | <select id="findByUserName" parameterType="String" resultType="User"> |
6.2.3 开发Service接口
1 | public interface UserService{ |
6.2.4 开发Service实现类
1 |
|
6.2.5 开发工厂工具类
在工厂中获取bean对象的工具类
1 |
|
6.2.6 修改自定义realm
1 | public class CustormerRealm extends AuthorizingRealm { |
6.2.7 修改ShiroConfig中Realm
使用凭证匹配器以及hash散列
以及在 getShiroFilterFactoryBean 中添加公共资源
1 |
|
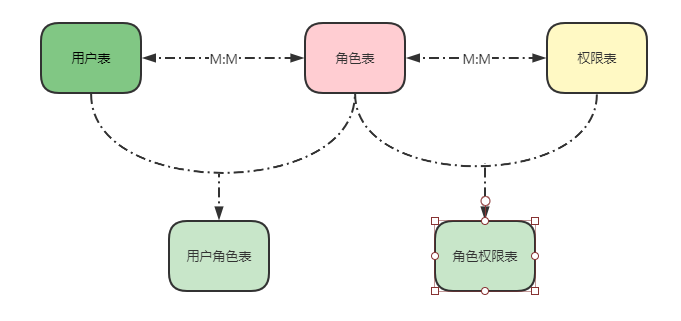
7 授权实现
7.1 没有数据库
7.1.1 页面资源授权
1 | <% contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %> |
7.1.2 代码方式授权
1 |
|
7.1.3 方法调用授权
- @RequiresRoles 用来基于角色进行授权
- @RequiresPermissions 用来基于权限进行授权
1 |
|
7.1.4 自定义Realm
1 |
|
7.2 连接数据库
7.2.1 授权数据持久化
1 | DROP TABLE IF EXISTS `pers`; |
7.2.2 创建实体类
User
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28import lombok.experimental.Accessors;
import java.util.List;
/**
* TODO
*
* @author YoungKai
* @date 2021/7/16 18:22
*/
public class User {
private int id;
private String username;
private String password;
private String salt;
//定义角色集合
private List<Role> roles;
}Role
1
2
3
4
5
6
7
8
9
10
11
12
13
public class Role {
private String id;
private String name;
//定义权限集合
private List<Perms> perms;
}Perms
1
2
3
4
5
6
7
8
9
10
11
12
public class Perms {
private String id;
private String name;
private String url;
}
7.2.3 创建dao方法
1 | User findRolesByUserName(String username); |
7.2.4 mapper实现
1 | <resultMap id="userMap" type="com.kenyang.springboot_jsp_shiro.entity.User"> |
7.2.5 Service接口
1 | /** |
7.2.6 Service实现
1 |
|
7.2.7 修改自定义Realm
注意:如果你创建了一个用户,并为这个用户授予了一个角色,但这个角色并未关联任何的 授权字符串,那么调用数据库获得的结果是 List<Perms> perms=[null],此时 perms已经被初始化,里面只有一个属性null,使用判空的方法无法判别,此时继续遍历会报出空指针异常,此时应当添加判断条件 perms.get(0)!=null
1 | package com.kenyang.springboot_jsp_shiro.shiro.realms; |
7.2.8 向数据库中添加信息
1 | -- ---------------------------- |
7.2.9 Index文件
1 | <% contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %> |
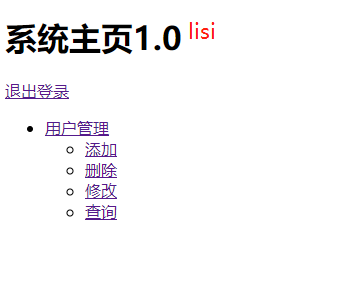
7.2.10 启动测试
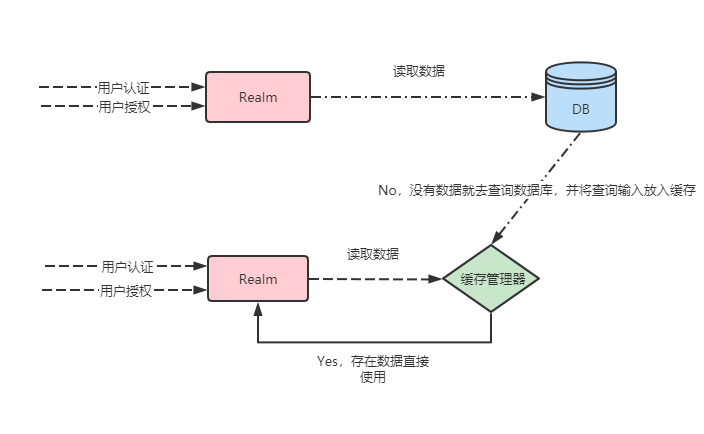
8 使用CacheManager
8.1 Cache作用
8.2 使用shiro中默认EhCache实现缓存
8.2.1 引入依赖
1 | <!--引入shiro和ehcache--> |
8.2.2 开启缓存
1 | /** |
8.2.3 启动测试
- 注意:如果控制台没有任何sql展示说明缓存已经开启
9 JSP中Shiro常用标签
1 | <shiro:guest> |